The PRISM story firmly changed course yesterday when The Guardian published a video interview with NSA whistleblower Edward Snowden. If you haven’t watched the interview, you should. It’s historic and fascinating.
The media has all but forgotten about just how the NSA gathers all this information from the companies listed in the presentation. After the story first broke, the denials happened. Then the NY Times connected some dots, and there were then further denials (“the government does not have access to Google servers—not directly, or via a back door, or a so-called drop box”). Then Snowden happened.
At this point there are a lot more things we don’t know than we do. But there are still a lot of dots to connect. So I’m watching the Snowden developments out of one eye while I continue to find peace in my soul for the PRISM stories that can’t find a way to merge into one believable narrative.
I’m working from the assumption that every statement by the companies involved is true, or at least arguably true. Besides the fact that I don’t think these people are liars, with all the leaking going on, they just don’t know what other information is going to explode onto the scene, and they have to hedge.
But still, unless you think the original PRISM document is a fake, or so completely muddled in how it explains things that it might as well be, there are some big questions unanswered.
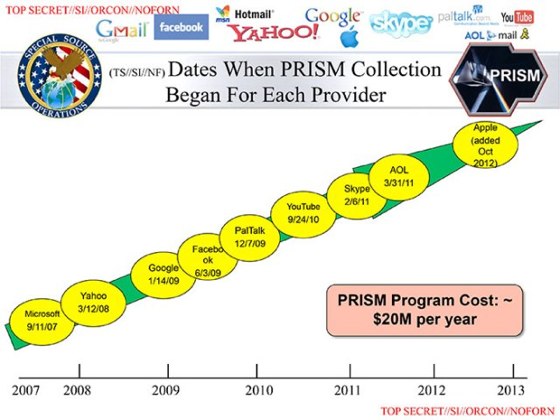
All of the denials and statements admit that the companies turn data over to the government “only in accordance with the law” along with various versions of how the companies review orders before complying.
I’ve spent a good number of hours researching these government orders, and talking to experts, over the last few days. I’m embarrassed to say that this was just not an area that I was particularly interested in, despite all the writing on the wall. To the best of my ability I’ve remedied that and am starting to push forward into some seriously grey area stuff. I am thankful to Wired’s Threat Level blog which has long focused on these issues. David Kravets work has been particularly edifying.
Here’s where we stand. I believe that #3 in my original post is still the most likely truth: “The presentation is real, and the companies are carefully drafting responses so that they aren’t technically lying.”
The government has a variety of tools under FISA and the Patriot Act to get the data they want (which is all of the data). We know a little about how National Security letters work from Google’s willingness to share data around those and the recent judicial challenges.
The Verizon vacuuming of all data over to the NSA, while horrifying, doesn’t apply to internet companies. Those companies must still comply with National Security Letters and FISA order, however.
The NY Times article changes the original allegations from The Guardian and Washington Post. There is no direct access allegation any more. The focus is now on special hardware lockboxes at company datacenters where requested data is moved for pickup by the NSA.
At first glance that sounds like a good idea. The government gets a court order, serves the order onto the company. The company reviews it and then sends the requested data into the lockbox. The NSA gets that data and the transaction is completed.
The only problem with this theory (from the NY Times story) is that Drummond afterwards said it’s not accurate – “not directly, or via a back door, or a so-called drop box.”
So let’s put Google aside for a moment and look at all the internet companies not on the Hot 9 list. Twitter, Amazon, Salesforce, for example. When they get a secret FISA order in they still must comply, without question. But they aren’t on the “direct access” slide. Clearly they are doing things, or not doing things, that make the process of getting their user data more complicated or just slower.
These Super 9 companies, in contrast, are doing something that makes them a headliner in the presentation deck. Twitter didn’t make the cut. Google did.
So again, taking Drummonds statements as true, what is Google doing that’s different than Twitter, and why is that thing making the NSA really happy?
I don’t know, but I have a guess.
My guess is that Google and the others have agreed to receive FISA requests in an automated way, process them in an automated way, and fire off the data in an automated way. That whole process could take a very small amount of time. Milliseconds for small sets of data, easy. Anything beyond that is from any human intervention at Google to read the order and decide whether to accept it. From what I’ve seen, it’s extremely rare for companies to push back on orders, since the secret FISA court always, without exception, tells them to settle down and get that data over to the NSA, pronto.
So Google complies, and the whole thing has been handled “in accordance with the law.” Given how important the Super 9 are to PRISM, it seems clear that responses from queries must come back pretty quickly, almost as fast as a normal search engine, for example.
That tells me there’s a lot of automation going on in a server or two (just don’t call them back doors or drop boxes).
Now here’s something new (to me at least) that also fills in some boxes. The NSA can begin surveillance on a subject for a full week before going to the secret FISA court for an order. In the last year every one of those orders have been granted, so it’s just a formality.
If I had been paying attention in May, David Kravets was already answering the questions I had last weekend. From his article Secretive Spy Court Approved Nearly 2,000 Surveillance Requests in 2012, he says:
The legislation does not require the government to identify the target or facility to be monitored. It can begin surveillance a week before making the request to the secret court, and the surveillance can continue during the appeals process if, in a rare case, the spy court rejects the surveillance application.
See section (g) here for the law behind his statement that the NSA can surveil someone for a week before going to the secret rubber stamp court.
So back to that “in accordance with the law” stuff that the Awesome 9 keep relying on. It appears to be quite legal to begin surveillance a week before getting a secret court order. That gives them time to determine if they’re barking up the wrong tree.
So, sitting around the NSA office one day an analyst has an idea. Like, “Hey, let’s find Republicans in Wyoming who have Facebook or Twitter friends with someone outside of the U.S. And then cross reference that with concealed carry permits. I think these guys might be gun running. Can I get a high five!?
Our guy fills out a form in PRISM, I imagine, with his query. The damn Twitter doesn’t do Prism and needs a more formal order, probably requiring someone to wake up the secret judge and tell him to get that stamp ready. And then they send off the order in a variety of ways and demand a response in 24 hours or something.
Meanwhile things are rocking on Prism. The Verizon data is all locked in and can map out his location over time as a map overlay, easily. Our analyst filled out the form, checked the “FISA approved” box (knowing this is legal because they have a week to go to court), waits a few seconds….and then boom there it is. Lots of data on gun owners in Wyoming with overseas friends. It went through the express line at Google, who noted the FISA approved stamp, and rushed that data right back down the pipe to the NSA.
Hey, bring up those Verizon records and see where this guy’s been. Damn, he goes to the range nearly every day. I wonder if he’s complying with every single Federal and state gun law. Let’s send an agent down to chat with him. And if he gives you any shit just show him this picture of his mistress Verizon sent over. That’ll shut him up.
WAIT! Here’s a frickin video! oh man, I’m sending this to myself. No, hold on guys, I’m doing this. Ok, now, show him this video of himself in a compromised position with his girlfriend and ask if we should sent it to his wife at their home address, it’s right here.
So after a day of looking at pictures of naked girlfriends and wives and ranking the top ten porn searches our perp Googled in the last year, our NSA guys still can’t find a NSA-type crime or figure out how they might stop a major terrorist event. Time to delete this data (which probably means shoving into an archive for later analysis and cross checking). And no bother going to the court on this since the surveillance ended before the week was up.
A few days after that a big package comes in from Twitter with 40,000 printed pages of information. They’ve complied with FISA, with a big middle finger. That stuff gets tossed into the scanning room and forgotten.
My scenario is ridiculous above, but it squares with the slides, it squares with the Snowden interview, and it squares with the many denials we’ve heard.
WE KNOW THIS: These nine companies have done something (we don’t know what) to make the NSA’s lives easier. So easy that agents are told to just focus on these companies (not Twitter or Salesforce or Amazon) for FISA orders.
WE KNOW THIS: The NSA can begin surveillance on someone(s) for a full week before they have to get the rubber stamp from the secret court (which has never said no).
WE KNOW THIS: The NSA routinely talks about mitigation efforts to purge U.S. people data; however, they always talk about these measures being taken after they have control of the data. What they should be doing is proving the data is clean before they grab it. But it’s way more efficient (and also evil) to dragnet everything and then try to cut the good data away from the bad. This is self evident from them taking all call data from all Verizon customers, even calls beginning and terminating in the U.S. They get the data, then make promises to the court that they’ll treat that data appropriately. Huge, Huge, HUGE incentives for misuse here based on efficiency arguments.
I GUESS THIS: The NSA “request” is fired off to Google and others as soon as these guys see a thread to pull, and they mark the request as FISA ordered (they have a week to actually get the order, which will be backdated). Google greenlights it as a legal order and fires over the data. If the data is useful the NSA wakes the secret judge up again to stamp it good. Otherwise they toss the data out and nobody ever talks about it again.
This is the world described to me by people I’ve spoken with who seem to have the best grasp of how FISA orders work, and how they might work in connection with PRISM. It makes sense when you realize that the NSA can order surveillance without court approval for a full week. Since surveillance needs data I assume that Google and the others send that data pronto to comply with the law. I doubt they ever see or hear about the actual FISA order a week later.
There’s a lot of educated speculation here, but if this is mostly right then we’ve got a system that works much like the PRISM slides say – it feels like direct access to a server. There are some things going on in between, like checking a box that the order is FISA compliant, but it seems to me that any request for data under FISA is looked at as a FISA order, as it looks like the companies have no ability to delay or object to the seven day period where surveillance can occur without the actual secret court order.
Thus, under this conspiracy theory, PRISM works just as planned, and just as efficiently, as it was described in the presentation.
Now, the only way for this to stop is for someone in one of these companies to pull an Edward Snowden, download some FISA orders and hop on a plane to Hong Kong. And then call me and I’ll fly over and do a really kick ass interview with you where you can tell the world the rest of the PRISM story. I’ll even start your legal defense fund for you and solicit donations, because you’re going to need it.
You’ll definitely want to plan ahead to avoid the fate of other patriots who tried to do what’s right with government demands. There are usually short trials followed by long prison sentences. See Joseph P. Nacchio as a sad example of a man doing what he thought was right and then being torn apart by the government for saying no to them.
This time it’ll be differen’t, though. Ecador, Iceland, China, they all got your back.
keep digging man. i don’t think this is the America they had in mind back in 1776… although it IS the one Orwell had in mind..
With all due respect, Ryan, back in 1776 they could not envision a world in which nuclear bombs existed and were dangerously close to the black market. I’m sure they never envisioned planes flying into World Trade Centers. Their idea of terrorism was probably a powder bomb in a public place or arson.
I suspect if the founders were able to look into our time, they would support the need for PRISM, just as our two most recent and polar opposite Presidents have. These are not stupid people and they have a lot more access to information regarding threats against us than we do. We elect government leaders to, among other things, keep us safe. It’s their job and we gave it to them. If we don’t trust the people we elect, why do we elect them?
All PRISM and its like do is ensure that all those nuclear bombs and terrorist activity is aimed at us. There are ways to fight evil. Being more evil isn’t what I consider acceptable.
Respectfully, I disagree. PRISM is not what makes the rest of the world target us. Wars for oil, drone strikes, and choosing sides in battles where we don’t belong is what makes the rest of the world hate us.
I don’t consider PRISM evil. I consider it necessary. Every developed country has its version of PRISM. Even those polite Canadians. If you’re suggesting that PRISM is ‘more evil’ than nuclear threats and terrorism, I sure don’t understand that kind of thinking.
I agree with Edward Snowden. PRISM is no longer just to defend against enemies and threats toward America. Enemies and threats, by the way, that a lot of folks outside of America (True or not?), (False or accurate?) believe are created to fear monger and brainwash your own people. And when people believe that the rest of the world is out to get them, they get wound up about supporting unnecessary wars and willingly blow the guts out of other countries citizens. And by getting the people to support unnecessary war because they’re afraid, they in turn gain support for their foreign policies of control and greed and natural resource security. Since the necessary WWII, a small handful of conflicts WERE valid human rights abuses that no one could stand by and watch. But true or not, false or accurate, step outside America and you’ll get a very different perspective about your government, your military, and what motivates your foreign policies – And your foreign policies are generally not seen as defense against terrorism or human rights protection.
The NSA with the PRISM program, and the patriot act, began with GOOD defense intentions years ago. But the meta data collected via PRISM on everyone of us, can tell those with access everything about who we are, what we do, how we think, every single move we make 24/7 … 365. And with a program called INTERCEPTS, a lot of technicians can find out anything about us, including all our texts, phone numbers, email conversations, photos, ect… within about 5 minutes via PRISM.
Folks with access to our information via PRISM are wasting no time abusing it. And I believe Edward when he asserts that this global blanket system of data collection will be increasingly used to abuse and control people on an individual basis, as well as a collective basis. Our data will increasingly be used to secure personal vendetta’s, for political blackmail. And eventually that rich data bank on the world, will be sold, in chunks and pieces, to the highest bidder who sees the value in the rich data that paints a scary accurate on-line identity about each and everyone one us.
So, yes, PRISM started off with good intentions, that’s probably. And every country needs their own version of what the NSA claims they stand for. But PRISM needs some major checks and balances in place to monitor the monitors and keep our information safer(er), and it needs them yesterday.
It seems our information has already fallen prey to the greedy elite and/or people who use it for their own agendas or sell it to make $$. And if PRISM was so great at finding terrorists, why didn’t it find the Boston Marathon threats before it happened? And there was also that airplane contract debacle that Booz Allen Hamilton got sued for. I could go on, but Booz Hamilton, is getting 5 Billion dollars plus in contracts per year, while not being any much good at finding any threats or enemies. Somebody is filling their pockets while sleeping on the job of what they claim to be defense of America.
But you know what Booz Allen Hamilton is not asleep about> You know what they are smart and good at? They’re magic at compiling the worlds most powerfully useful, telling and accurate data bank on every single person in the world. PRISM began with good intentions. But we’ve all seen greedy power hungry human nature. And with this much money and power at stake, the golden data within the confines of PRISM, and the CONTROL SWITCH of the entire system becomes one of the hottest commodities ever. Ever. Everrrrrrr…
Just keep in mind, as the intrepid tech reported, that there are other downsides than just long prison sentences 🙂 …Google or rather DuckDuckGo these days… Costa Tsalikidis (Security Technician Vodafone Greece) and Adamo Bove (Security Specialist at Telecom Italia) – links also below – both strangely committing suicide after a government illegally tapped mobile networks.
Circumstantial – but the NSA don’t appear to use senior management approval for such programmes and security/operations specialists in target companies have a high propensity for ‘suicide’ when these things start to unravel.
Of course, these things don’t appear limited to the US and the NSA – also checkout the strange death of Shane Todd in Singapore, working on a sensitive program for Huawei.
If you’re that security / operations guy who is approached by the security services, who wants to do the right thing for his country, but also has suspicions of pretty negative consequences for refusal – these are big boys games afterall – what do you do? I would probably think twice before hopping on that plane for an interview with you.
Costa Tsalikidis: http://en.wikipedia.org/wiki/Greek_wiretapping_case_2004–2005
Adamo Bove: http://www.edri.org/edrigram/number4.15/italy
Shane Todd: http://en.wikipedia.org/wiki/Death_of_Shane_Todd
I think you seriously underestimate the founding fathers, given the rapid advancements in weapons technology in their own era, and THEIR OWN experiences in rebelling against an oppressive government, I don’t think they would make up their minds any differently if they knew what was going on today.
It is also pretty naive to assume that those in charge must know what they’re doing and have our best interests in their hearts. When history has shown time and time again that this is not always the case – and we damn well better be careful about it.
its all relative. no, they didn’t have nuclear bombs in 1776, but they did have an overbearing government that snooped on its people. they had spies within the populace and anyone against the British government was brutally punished.
9/11 was a substantial loss of life, but the steps taken by the US govt to prevent another attack have caused much more death and global hatred than anything Al Qaeda could have dreamed up. the cost of the wars waged in response to 9/11 sank the US into an economic depression, which had a ripple effect across the entire world. economic recovery will take decades, if it ever happens at all. this is an acceptable cost for your “freedom” and “security”?
when people say they are willing to give up so much freedom for “security”, they look like little chickens to me. they are essentially saying, “i am willing to be watched 24 hours a day just so no one bothers me.” its horrifying.. grow a pair..
“grow a pair..” Our latest keyboard warrior – Bishop the Bold!
I’m glad you agree it’s relative, and I’m sorry you can’t comprehend that nuclear devices and attacks on the scale of 9/11 are game-changers, not natural progression of conditions in 1776. I think it makes it pointless to have a dialog with you because you’re more focused on a romantic ideal than on our modern reality.
Your second paragraph make a a good but misses the mark. Yes, the corrupt oil-driven push into Iraq and our 11-year stay in Afghanistan has created a lot more new America-haters. Probably more than we started with. It’s angered a lot of Americans too, including me. However, the cost of those wars raised our debt but did not push us into a depression with a ripple across the world. In fact, the collapse of the real estate market triggered a collapse of the credit markets, which triggered a collapse of the banks. The ongoing erosion of the Middle class hasn’t helped. Clinton planted those seeds and Bush did nothing to head off the collapse. 9/11 wasn’t even a twinkle in our eyes when those seeds were planted.
Your last paragraph is based on a false assumption, because I don’t think people ARE giving up “so much freedom”. If you like living in a safe society, there are costs you have to be willing to pay. You have to earn security, it doesn’t come for free. I think you need to get out in the world a bit more. MI5 openly admits that they are monitoring electronic communications but the Brits don’t seem to mind as much. Perhaps that’s because they’re a little less naive and little more experienced with bombs going off in buses, pubs, subways, etc.
Your pointsg lays bare the truth
THANK YOU. I thought no one in the tech industry (least of all any of the journalists who are often in bed with those they cover) would approach this critically. This is a story that every single tech journo should be all over – pushing back against the companies’ denials. Instead they seem only too happy to accept the denials and are even minimising what this information could possible tell us. This says something about the incestuous nature of the coverage.
I think an important question everyone is not asking here is: What is Paltalk? It sounds sinister.
Terrorism is not an existential threat to democracy, but mass surveillance is.
Whats sad is the most Americans are not watching these news unfold and have no clue of the impact and are not interested as no one ever watches the news or Read the news, it “Too depressing”.
Reblogged this on Information Techology and commented:
well…..
Google’s chief architect on user data – how much latitude in his responses?
Great work! Finally someone showed those journalist morons how reporting is done 😉
I’m a technology guy. So when I’m thinking about the same question as you, I’m asking myself, “How can all those statements be true using only technology?”
The result of Mark Klein’s disclosures seem to be that there are fibre splitters in backbone providers that send copies of all the data that passes over that fiber to the government. We don’t know how many of these there are, nor what percentage of high capacity links they snoop on. But because there are few top tier providers, and because traffic is routed through
There are also credible stories of underwater intercepts of submarine fiber optic cables. Or take a network operator like FLAG; they need to hire Tyco to go out and repair fiber breaks. The operator probably cannot detect if a fiber goes back into service with a different loss rate due to the vagaries of at-sea fiber repair, or because Tyco had been pressured to add a fiber splitter into the new coupling by the NSA. (This is hand-waving conspiracy theory stuff; but the engineering, physics, and commercial relationships allow this possibility.)
It would be a monumentally difficult software and network engineering project to write the code that could reassemble the TCP flows visible in those network traces in realtime. But it would be possible. The result is that the government could retain only the reassembled content, letting the packet flows themselves drop in to the bit bucket. And the content providers themselves would be unaware of it.
The dates on the PPT could be the dates that the software update capable of decoding a given system’s content was pushed out. Before that date, the NSA was seeing the packets, but inundated by them and ignoring them. After that date, unencrypted content to and from that particular company might be stored into a database.
Once substantial numbers of taps and “content reconstructors” like this were in operation, hacking the legal system like you describe would be superfluous. My understanding of the NSA’s culture is that it values stealth and technical prowess over legal threats/manipulation.
-jeff
PS: NSA was not likely employing Edward Snowden in Hawaii because of the good work/life balance for their employees. It is likely there because it is a key choke point for trans-pacific fiber routes.
PPS: Even back in 2000, Applied Signal Technologies (now part of Raytheon) was able to process tapped circuits up to 2.5 gigabit/sec and record the emails, faxes, voice calls, etc on them. https://www.fas.org/irp/eprint/ic2000/ic2000.htm
I think you’re spot-on! I’ve been trying to get people to listen to this notion ever since this story broke. This is the ONLY explanation that makes sense, and it shows the extent (and expense!) the NSA is willing to go to to try and know everything about everybody. And since they are “impartial” they don’t care if you’re Obama’s brother or a Tea Party organizer, right?
Awesome…the only part you’ve missed is (according to nyt or wpo) is the co-location of NSA hardware in the big-9 data centres. What does this do?
You made me realize: The query / FISA request that Google gets may not contain any foreign piece because the foreign connection could come from Verizon or Facebook or somewhere else. So Google’s lawyers have no way to say or push back to say this is domestic only, they can’t see the other piece. Remember somewhere it say these request are sent 1st to the FBI to check to see if the target is foreign? That’s what’s happening, I just need to include some foreign connection from Verizon or Facebook in the PRISM web-app and it will send the request to all the PRSIM players only 1 of which will have the foreign piece. OR stretching it here a little, they lie to all of them saying the foreign piece is in the other guys request. There is now way for the companies lawyers to reject this.
Before reading this I assumed that Google or whomever could, try at least, to reject a request based on the fact it was domestic only. But according to NSA, Google can’t see the whole picture, so shut up and give us what we are asking for.
Without being able to reject a request based on lack of ‘foreign-ness’ I’m not sure that when Google’s lawyers receive these request there is much they can do other than rubber stamp them.
Google did say their lawyers review each and every request. I imagine some poor souls just out of law school setting at screens 24/7 approving everything that comes by.
Excellent!
The only thing that scares me more than all of this government spying is the majority of sheeple who are OK with it. Never mind the thousands who have died over the past 300 years to secure the liberties that so many Americans are now happy to trade in for a nice, warm government-embroidered woobie.
I’m with you Jon. It’s scary.
I think Rick Falkvinge’s conjecture squares more consistently with the slides and the statements from the companies:
http://falkvinge.net/2013/06/08/so-just-exactly-what-is-nsas-prism-more-than-reprehensibly-evil/
With his conjecture,
1. Nothing that could be even remotely construed as any sort of “backdoor” or “dropbox” need be used.
2. It provides a much better explanation of the relevance of the slide entitled, “Introduction: U.S. as World’s Telecommunication Backbone.” (If the NSA has access to their servers, this slide is a bit of a pointless non sequitur.)
3. It adheres more closely to the analogy of real (optical) prism.
Essentially the answer to “what is Google doing that’s different than Twitter, and why is that thing making the NSA really happy?”, under his conjecture, is that Google gave the NSA their private keys and/or their certs. I would further speculate that Google assisted the NSA in setting up their own “shadow” servers for optimal searching and compression.
Your example of the NSA spying on a US citizen for a firearm-related federal crime is invalid. Last I checked, domestic law enforcement (ATF, FBI, DEA, etc) cannot use intelligence resources gathered from Patriot-act/terrorist snooping.
Yes indeed. And The information you give the IRS is supposed to be just between you and the IRS.
This administration has proved more than once that it will use any agency of the government to get a political advantage over its perceived enemies.
Forgive me if I seem skeptical.
Ecuador
Inverted values: an American citizen takes refuge in China due to American authoritarianism. Modern times.
All this surveillance has as its main argument: national security. Protect Americans from the dangers outside. It’s necessary to anticipate before evil occurs.
What evil is this that only the USA are likely to suffer? What are these dangers that only Americans have? Would not it be easier for the USA to adopt a less aggressive policy with the rest of the world rather than shouldering with all kind of result that they themselves cause?
I think the problem isn’t the PRISM and the acts of the NSA but the american culture of fear, a culture of terror, the collective thinking that someone is trying to destroy the country and the rest of the world is the enemy.
This will not end. PRISM is not the problem, neither the authoritarianism of the NSA. The problem is the american culture of fear.
Twitter’s firehouse is readily available through authorized providers such as DataSift and GNIP. The same providers are used by many social analytics services that track Internet memes and social campaign performance. Since Tweets are meant to be broadcasted out, most Twitter data (except private tweets) wouldn’t require any special access.
“The Verizon vacuuming of all data over to the NSA, while horrifying, doesn’t apply to internet companies. Those companies must still comply with National Security Letters and FISA order, however.”
I thought so as well, but am not so sure now. William Binney, former NSA whistle blower points out a fascinating detail which I believe many have overlooked in this interview with Democracy Now, and I am quite compelled to believe his analysis.
“WILLIAM BINNEY: Well, the only surprise I got—I mean, the PRISM program, I had assumed was going on anyway. But the court order that was published that showed the—it showed the serial number at the top, on the top right side of it. It was 13-80. That meant it was the 80th order of 2013 of the FISA court. And if that order was typical of all those other 79, which was authorizing them—or ordering them to turn over records that would—to NSA, even though it was the FBI doing the request, it shows you the relationship between FBI and NSA. It’s really close, and they’re depending on NSA to do their processing. But what it is, what that tells me, that serial number told me that, gee, if all those orders addressed individually every quarter—this was the second quarter of 2013—then there would be, at a minimum, 40 companies involved in this activity. So, it would be telcoms—it would be a mix of telcoms and Internet service providers.”
http://www.democracynow.org/blog/2013/6/10/inside_the_nsas_domestic_surveillance_apparatus_whistleblower_william_binney_speaks_out
“The Verizon vacuuming of all data over to the NSA, while horrifying, doesn’t apply to internet companies. Those companies must still comply with National Security Letters and FISA order, however.”
I thought so too, but am not so sure now. Interesting little tidbit from an interview with William Binney, former NSA whistleblower, and Democracy now. While I personally have no first hand experience with these matters, I am compelled to believe his analysis.
WILLIAM BINNEY: Well, the only surprise I got—I mean, the PRISM program, I had assumed was going on anyway. But the court order that was published that showed the—it showed the serial number at the top, on the top right side of it. It was 13-80. That meant it was the 80th order of 2013 of the FISA court. And if that order was typical of all those other 79, which was authorizing them—or ordering them to turn over records that would—to NSA, even though it was the FBI doing the request, it shows you the relationship between FBI and NSA. It’s really close, and they’re depending on NSA to do their processing. But what it is, what that tells me, that serial number told me that, gee, if all those orders addressed individually every quarter—this was the second quarter of 2013—then there would be, at a minimum, 40 companies involved in this activity. So, it would be telcoms—it would be a mix of telcoms and Internet service providers.
AMY GOODMAN: You know, there’s been a lot made of the document that shows that Verizon is handing over its information.
WILLIAM BINNEY: Right.
AMY GOODMAN: But that’s just because that’s the document they have.
WILLIAM BINNEY: Right.
AMY GOODMAN: Do you assume we’re talking BellSouth, we’re talking AT&T and the other corporations?
WILLIAM BINNEY: Yeah, plus the Internet service providers, and that would add up to 80 orders from that court that—this year so far, for two quarters. So, each company would get an order each quarter to do that. So that’s—you have to divide 80 by two. And that’s the minimum, OK?
interview can be seen in full here: http://www.democracynow.org/blog/2013/6/10/inside_the_nsas_domestic_surveillance_apparatus_whistleblower_william_binney_speaks_out
I am more surprised by everyone’s reaction to the Prism news than I am about the news itself. Did people really think that this was not going on? Of course this was going on.
Did they totally miss all those seasons of 24?
Thank you Mike for sticking with this. This truth will eventually be known.
Surely the reason why twitter “didn’t make the cut” is they already have a firehose of their public data you can buy directly from them or slices via partners. It would not be a big leap to simply add DM messages to a firehose and charge the NSA a large fee for access?
The minute somebody says “Connecting the dots” it means that they are reaching and have no evidence to back it up. All speculation.
To retort…
View at Medium.com
The next logical step is that the US residents will be denied to leave the US. This is what the USSR did in fear of the secrets to be taken out of the country.
Right.. because that’s how logic works. You’re allowed to go from one point to any other random point in a single step.
Haahhaha. I’m not too bright today. Great post!
I posted this theory on my G+ feed the first day it was leaked, that PRISM amounted to an automated-NSL-request-and-response management system, like an issue tracker. Click a button to mail an NSL request electronically, notify employee when company approves, go pick up the data automatically.
PRISM is an NSA issue tracker with auto-import essentially.
But someone else pointed out to me something more interesting. All companies which provide voice telephony, even VoIP, have to comply with CALEA, which means they have to install equipment maintained by the FBI which allows intercepts of Voice calls via search warrant.
Once Google added Voice/Video chat, they might have had to comply with this, just like Skype. Ditto for Apple and Facetime.
The Washington Post said something about the NSA tasking the FBI in this pipeline. Therefore, PRISM may be abusing CALEA devices which companies are compelled to install, by leveraging them for intercepts of voice in ways that don’t fit the law.
So, revised theory:
For email and non-voice data, PRISM sends an NSL to company, waits for approval, then hits a REST API to pick up the goods.
For voice, PRISM sends request to FBI, who then commands CALEA device for intercept. No company action required?
Still, the coverage of this was hyperbolic and I think Arrington should retract calling the companies dishonest.
What was known before the PRISM leak?
That tech companies comply with NSL/FISA requests and turn over individually targeted user data. The Google Transparency Report makes this clear. Google for example, has not hidden this fact.
What do we know after PRISM? That the implementation may be streamlined by some enterprise apps. Rather than mail snail mail legal letters to company lawyers, the process may be automated by digital requests and digital approvals.
So really, there’s no big scandal here. The so-called “drag net” that is alleged, purportedly given the NSA unrestricted access to just look up any information on demand without company approval ala Verizon, has been walked back.
The real scandal is these NSL requests with gag orders. You can’t really blame the tech companies for these, and they are trying to fight them, but with the Executive, Legislative, and Judicial branch, not to mention, according to polls, the American people, arrayed against them, there’s no much they can do.
One must see Google/Facebook/et al as operating in hostile territory to liberties, like China. When we think of Google in China, we think of them being forced and compelled to do things they are against, like censor results.
Now we have to view the US itself as “hostile territory”, with the companies being forced to do things they would rather not do — turn over personal data in increasing scale — if only for reasons that privacy breaches could destroy them.
The US should not be a country where you need to seek asylum from, or perceive that your business has to act against civil liberties in order to do business.
If twitter really wanted to piss off the nsa they could send the data on atari megafile 44 disks.
If Twitter really wanted to piss off the NSA they could send the data on Atari Megafile 44 disks.
“My guess is that Google and the others have agreed to receive FISA requests in an automated way, process them in an automated way,”
Google has made it clear that FISA requests are reviewed by a Google employee before action is taken. I believe this is also the case for the other big data companies.
What I would suggest is looking into the CALEA framework on how that system was designed/implemented, then see how easy it would be to automate that system with a permanent warrant.
So what you’re saying is: it’s a secret API. Abstracted, complete access to a service provider, without having direct access to any servers or having to save data anywhere else. Requests are made, presumably with some metadata about the legal justification, and data comes back.
If you’re planning to interview a whistle-blower in Hong Kong, then you should use PGP, or better yet, Bitmessage. Let the whistle-blower contact you safely so he can’t be stopped before getting into the plain.
Thank you so much! This post is so critical and so insightful. Happy to see you trudging through the morass and putting pieces together.
PRISM is just another step in the Illuminati Pyramid, get informed before it’s too late http://www.illuminatiornot.com/prism-%28surveillance-program%29
Holy S*. I’ve never seen real journalism like this. Is this what journalism is supposed to be?
Isn’t this more or less what google says they do here: http://www.google.com/transparencyreport/userdatarequests/US/?
Court mandated government requests come in, they validate to make sure its fine, and then give the data back.
The issue, in my opinion, is less the companies giving data when a court asks for it, but the large scale copying of all internet traffic by the NSA to “secret” warehouses. If they publicly acknowledge that the warehouses exist, legislation can be drawn up as to who, how and when the government can access the data.
Last year the government asked the rubber-stamp-FISA-court approximately 1,789 times for permission to access reports from the database. They were denied exactly 0 times. The FISA-rubber-stamp court never says no. Yet the Obama admin takes great pride in “the numerous safeguards in place” and that they did not break any laws. What the Obama admin fails to see, and which is not sitting well with many American citizens, is that they didn’t have to break any laws. The White House approved activity of NSA seems to be no different than any repressive regime who put laws in place that allow them unfettered rights to monitor, control, jail and do whatever they choose.
This holds water. Google and others already have such a system for DMCA takedowns and it stands to reason that it would get adapted for other government inquiries. And once it’s automated, the tech companies can claim plausible deniability because they have no knowledge about what if any data is being requested. It probably runs on a darknet so nobody will notice massive amounts of data flowing to somewhere in Utah (except the telecoms but they’ve been the US intelligence community’s familiar since the 30s). And the spooks won’t talk because they see it all as a game. The only weak point is that someone has to hire some grunts (Snowden) to set everything up.
This is very good. Why don’t you ask to publish this on TC where you used to work. Their articles are all B.S. on this subject. They linked to this from their site. I have a feeling snowden was a bit overdramatic and slightly too quick to cry conspiracy theory but he was possibly right.
He was a bit over dramatic when he started talking about the triads killing him at the behest of the US government and when he started saying that he could have tapped Obamas computer. The former demonstrated a degree of paranoia and that latter a propensity to chat horse shit.
That was his moment and he should have been more honest about it and maybe more humble. Zuckerbergs denial with the starting sentance calling it “outrageous” suggests that he is either a liar ( as is his past form ) or he genuinely doesn’t believe that that sort of access exists.
Company insistences there is always a human in the loop plus ex-NSA member testimony that returns are nowhere near instantaneous argue against your theory.
The Nine, as you put it, could merely be the only nine that take a request under consideration electronically, rather than wait for a formal legal document on paper, combined with an agreed-upon expedited method to return the results. In the case of a legal request, you’d almost always be talking about hard media returns, notorization, etc. The possibility of any return within a week as opposed to three or more that legal could potentially add would be more than enough to make those firms seem the more cooperative ones.
Good point about the week waiting period loophole, but I’m sure the legal opinion would be that the seven day period applies to how far back from the date of request the user data shall be made available. So if they get the request Sunday, they may feel they are only legally compelled to provide all data from last Monday on. Different than what you’re stating.
Also remember most of these requests are not going to be one-time, but standing-query: everything going into/out of a foreigner’s gmail box from now until three months in the future, for instance. Even a modestly expedited delivery method would offer huge advantages in that situation, as once satisfied it satisfied the legal requirement, the company wouldn’t recheck on a per-communication basis, so setting up that kind of forwarding rule would require some automation. The Nine may be just the only ones that have agreed to do that right now.
You have to ask yourself why, besides patriotism, would the Nine agree, and what does that say about what they are agreeing to? Clearly they are achieving some work-savings here, as well, while still being able to say to themselves they are only sending what they would have sent eventually anyway. These nine may be the only ones that have to deal with a sufficient volume of requests to swamp their legal team if treated as formal legal request and response, particularly in the case of standing queries, and have streamlined process accordingly. There is nothing inconsistent in their or the NSA’s statements if you assume that. The original article, though, seems rather alarmist if that’s all we’re talking about: anyone who’s thought about it would have assumed this would have been going on already.
The correct answer is to do to government what they are doing to us… Instantly pull data on every public employee, send out drones, watch the cops, the whole 9 yards….
And the funding will come from $1K annual tax credit to watch the government:
http://www.morganwarstler.com/post/52547186796/radical-surveillance-of-the-government
There’s no reason we can’t go on offense, tis plan will be incredibly popular with voters of all stripes.
Everyone except public employees.
There is one more thing… The costs are supposed to be just 20 million $, now how is that possible ?? This amount of data is certainly much more expensive
Hi Mike- been a while since I spoke to you –
A 20 year Web Veteran (with prior service into US ARMY Signal)- its not very sophisticated to simply grab IP data and separate even Telecom trunk lines that are encrypted and mux’d. This stuff is way more powerful that you even know Mike.
As a Big Data enthusiast (not yet expert) Hell- Mike- spend a weekend playing with Radian6 and Sysomos- you can get in near time (near real time) all the information you are stating above. YOU CAN DO THIS PRETTY MUCH WITH BIG DATA TOOLS NOW. Its spooky- and something you should really spend some time looking into. Everything you just wrote could pretty much be done with off the shelf big data tools, sans naked port pics within the systems, but everything else, including GPS coordinates- who they influence, their psychological profiles, and more all from the text in twitter/FB/ forums and more. yep. As the bullet enters my brain I love Big Brother
As the slide illustrates… does PRISM really only cost $20M annually? It seems to be very cost effective if they can actually pull together a technology of this scale for that annual cost with 3rd party contractors. #confused
If the prism program finds anything, I think they should send out their drones.
Michael. thanks for the logical analysis – I bet you’re right on most aspects. (So much of the discussion is reactionary, conflating different issues, and biased.)
I have concerns about government that’s big, powerful, intrusive, unaccountable, secretive and untrustworthy; and there are issues with something like PRISM, which is there to help us, and for the most part it does, but with some big dangers.
We need to maintain the distinctions between the different programs and databases: MARINA contains call detail records from Verizon etc. PRISM/US-984XN refers to email, chat, videos, photos, VOIP, social data from GOOG, YHOO, MSFT, Facebook, etc. STELLAR WIND/RAGTIME monitors e-mail communications, phone conversations, financial transactions, and Internet activity. (FAIRVIEW, BLARNEY, etc.) refers to “upstream” IP listening. PINWALE is the email database. ROOM 641A is the secure room at service providers where the NSA receives the data.
Most PRISM data is posted in the clear, voluntarily by users (who are now outraged by the loss of their privacy).
“Gather” and “Collect” refer to retrieving, indexing, and querying, not “spy”, “read”, “watch”, “track”.
Sure, FISA Section 702 requests are made case-by-case, as officials and CEOs have said. PRISM and the other programs are much more than these requests.
I think the NSA gets their own copy of the data, and not just in response to a 702 FISA request.
To use of any large amount of data requires low latency queries and responses. The NSA needs query times measured in seconds, not days. Therefore the data is indexed – at the NSA. Why? Because of the companies, only Google and possibly MSFT, would have the resources to satisfy all the search criteria of the NSA (they will require an elaborate combination of boolean search criteria and features like wildcard, reverse wildcard, soundex (how DO you spell “tsarnaev”?) etc. That’s why the NSA building the Dark Star facility with capacity of Zettabytes. (that ain’t just “meta-data” mr. president).
It’s not enough to send a request to each company and pull some records and then try to make sense of it. To be effective they will be dynamically doing query refinement, pivots, and joins across these exabytes of information. If they’re going to thwart terrorist or other enemies, they’ll probably be continuously pulling the data from Rooms 641A and indexing it for future use. Whether we like it or not, this isn’t “ready” our email, nor is it “listening in” nor is it “spying” or “tracking”. It’s indexing, and it’s entirely machine automated – none of the data would mean a thing to a human. When they say it’s “legal” or supervised by a FISA court, they mean the process of continually indexing but not peeking until requesting a warrant.
When an investigation is underway, to ensure compliance, the analyst would specify their query and fill out a form (that later gets approved for a warrant after the fact). This would then “unlock” the system for the approved query (whether that means actually decoding encrypted data or just enabling access). It’s unrealistic to think that the NSA isn’t searching across multiple databases that have already been indexed from many sources.
So what’s the problem?
Well, if we want to maximize the NSA/CIA/FBI’s chances of catching/stopping bad guys, we want them to have the tools to quickly put the facts together, just like any of us would use a search engine to plan a vacation, choose a plumber, or due diligence a job candidate. But we don’t like OUR INFORMATION in that database.
I think there are three main problems:
1. FALSE POSITIVES. The database used according to design, with the proper restraints and no mistakes would only catch international bad guys. But mistakes will be made and people will be unnecessarily investigated or even falsely charged , just like cops occasionally shoot innocent people. We don’t abolish the police because we need their services. But we do look a ways to reduce police shootings (or false positives in PRISM)
2. ABUSE. Someone breaks protocol, and uses the PRISM system to look up an ex, embarrass a public official of one party or the other, or harass someone they don’t like. This would be a real issue, and there needs to be oversight and prosecution for abuse. However our trust of the government is at a low. It appears that officials at the IRS, DOJ and other departments ARE in fact willing to break the rules to target and harass people they don’t agree with.
3. OPPRESSION. More than spot cases of abuse. Perhaps not today, but some day some administration and its intelligence apparatus would have an extraordinarily powerful tool to oppress private citizens.
What exacerbates the issue is that people in the government and business seem to be utterly unable to tell the truth, simply and clearly. Sometimes it’s because the parties are subject to gag orders. But it seems everyone from James Clapper, to Louis Lerner, to Eric Holder, Susan Rice etc. etc. seems to be constantly contradicted or exposed as being less than truthful, whether it’s IRS Targeting, tapping journalists, blaming Benghazi on a video, the existence of WMDs, a search for yellow-cake Uranium, who ordered Fast and Furious putting automatic guns in the hands of Mexican drug-lords, drone strikes, or… the nature of PRISM. So we trust them even less – while we’re being asked to trust that this system will be free from abuse. Yet we need these programs to catch bad guys. Quite a dilemma – and not as simple as people make out.
What do you think of Steve Gibson’s theory: http://twit.tv/show/security-now/408 ?
Great post. PRISM is another reason why it’s hard to view the Democratic Party as an institution worthy of our support:
(http://andrewhanauer.wordpress.com/2013/06/13/a-politics-of-love/)
The other question that I keep coming back to: why all the time and effort fighting terrorism when it kills far, far fewer Americans than any number of other plagues? A lack of government regulation and oversight leads to a fertilizer plant explosion that kills 15 people is almost an after thought compared to a terrorist bombing that kills 3.
Maybe we should let OSHA spy on companies instead of the NSA spying on us.
The answer to your question is simple: the time and effort being invested is based on what ‘could’ happen, not on what ‘has’ happened. We live in an age of nuclear and biological weapons, surface-to-air missiles, etc..
Your point about other plagues is valid. The number of Americans killed in handgun homicides in 2012 alone is roughly equal to the total number of Americans killed by war and terrorism over the past *30 years*.
Facebook reveals 9000-10,000 US data requests in second half 2012 http://newsroom.fb.com/News/636/Facebook-Releases-Data-Including-All-National-Security-Requests
Companies’ plausible deniability.
Let’s take a look at your https-protected sessions with gmail (we have to be technical here to sure important practices). Your browser’s request, in secured form comes to load-balancing server, which shall send your request further into company’s cloud. But to know were exactly your request must go in the cloud, secure https envelope is opened, message is partially read, and is send further, usually as http, as it goes inside of a company’s data-center.
Now, recall revelations about funky optics splitter technology that is used to copy any data on internet backbones. So, all goverment guys have to do is to have a room, with no “direct access” to servers, but with all internal optics passing by. Clip some optics splitters on, and copy all that goes in and out. On one hand, company does not know what happens, as noone is allowed into a special room, and who cares about suspicion. On the other hand, government has all your data (email, chats, voice, video, searches) in unencrypted form.
More people to quit social networks after #Prism news according to latest survey findings http://tinyurl.com/k5gjsnh #NSA
If some one needs expert view concerning blogging and
site-building after that i propose him/her to visit this blog, Keep up the nice work.
If I start a company outside of US, does NSA have the legal rights to ask me for confidential data? If no, why don’t those companies move out of US?
Also, if I develop a web application which records and save data only for a short amount of time, can they force me to save and retrieve that data? Meaning, they can force me to change my app way of functioning?